A Complete Guide to Enterprise‑Grade Custody
Summary for busy executives
- Digital assets are now core to payments, markets, and treasury. Stablecoins set new records in 2025, and tokenized Treasuries passed seven billion dollars in value.
- Enterprise custody is security plus governance plus compliance. You need all three to scale.
- The right architecture depends on your risk model, regulatory perimeter, and operating model.
- A strong vendor should prove resilience through audits, uptime, incident playbooks, and transparent SLAs.
- Treat custody as program management, not a feature. Budget for people, process, and continuous testing.
What enterprise‑grade custody is
Custody is the secure control of the cryptographic keys that move digital assets. In practice, it is a stack:
- Key management that prevents single‑point failure
- Policy and controls that decide who can move what, when, and where
- Operations that reconcile, monitor risk, and prove compliance
Your teams will use custody for three jobs:
- Safekeeping for reserves, client assets, and inventory
- Settlement for trading, payments, staking, and on‑chain finance
- Controls and reporting for auditors, boards, and regulators
Two market shifts make this urgent. First, stablecoin capitalization hit an all‑time high in mid‑2025, signaling broad institutional use. Second, tokenized U.S. Treasuries crossed seven billion dollars on public chains, turning tokenization from a pilot into production infrastructure.
Source: https://ww.pwchk.com/en/risk-assurance/digital-asset-custody-report-jul2023.pdf
When individuals or businesses hold digital assets like Bitcoin or Ethereum, they control unique cryptographic keys that grant access and enable transactions. Losing these keys means losing assets forever - there’s no “forgot password” option. As institutional investors - from hedge funds to pension funds - enter the market, the stakes for secure, compliant custody have become too high for self-managed solutions.
These complex requirements spurred the rise of professional custody services, driving a surge in assets held by custodians. What began as a niche offering for early adopters has become critical financial infrastructure, safeguarding trillions in digital wealth.
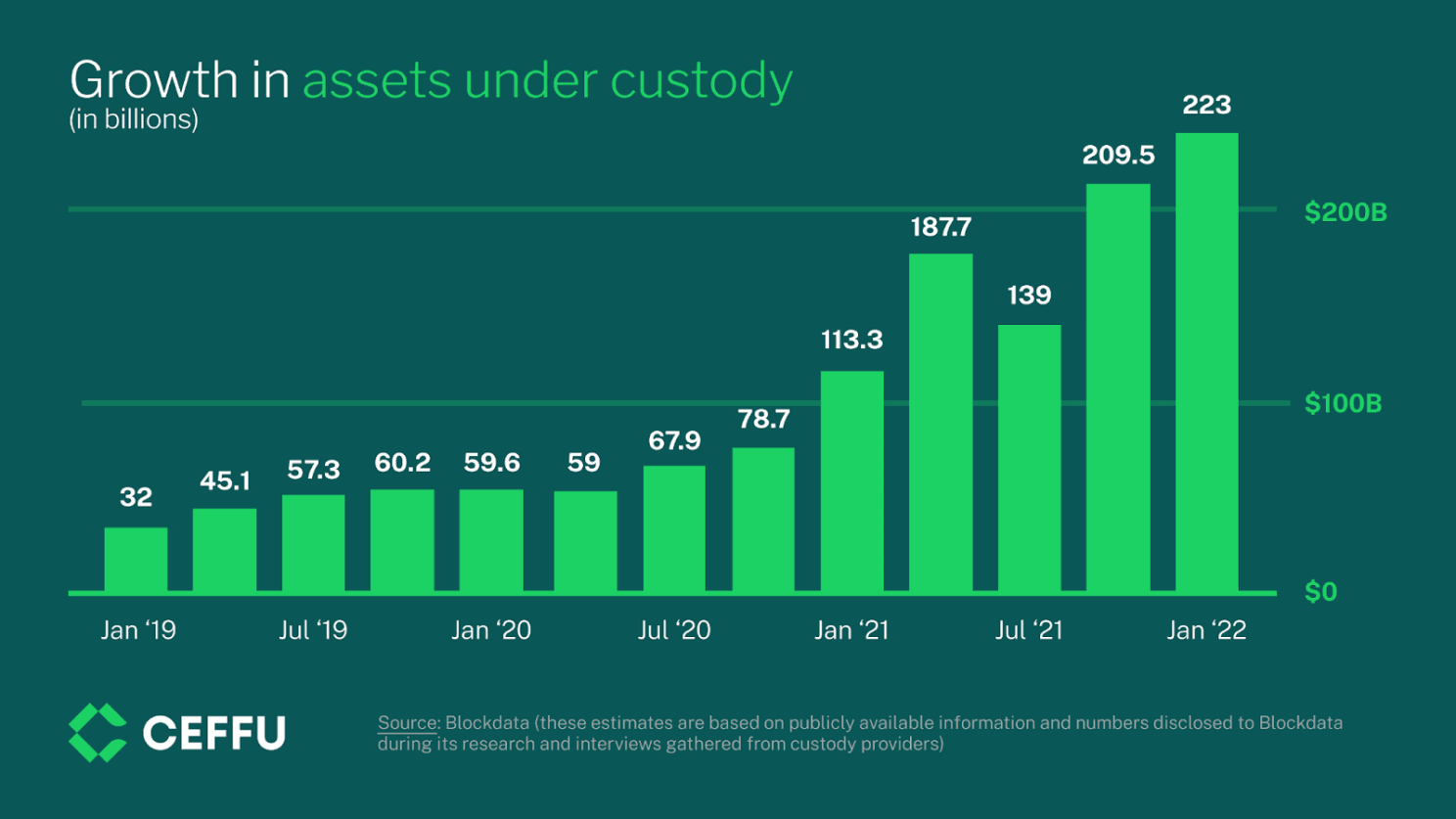
Why custody matters now
The cryptocurrency industry has witnessed numerous cases where individuals and businesses lost millions of dollars due to lost private keys, security breaches, or inadequate storage practices. Professional custody services eliminate these risks by implementing institutional-grade security measures that would be impossible for most individuals or businesses to achieve independently.
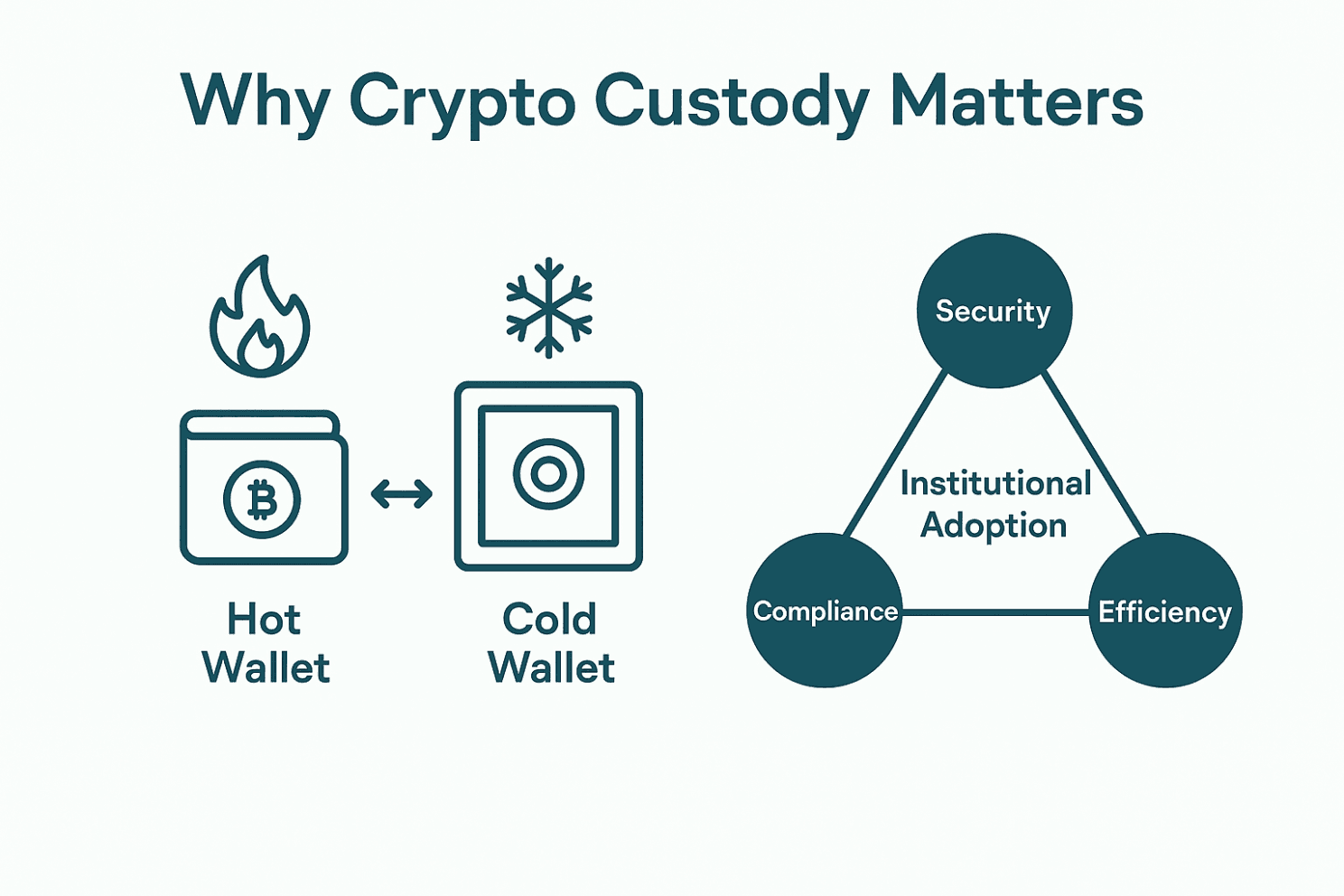
- Security: Cryptocurrencies are stored on blockchains and controlled by private keys. History shows that major hacks (e.g. the Mt. Gox and Coincheck breaches) led to massive losses. One of the most common ways custody protects assets is by keeping most funds in cold storage (offline) and only a small portion in hot wallets (online, for liquidity). But a professionally managed custody solution of Scalable goes beyond that – it greatly reduces these risks by using offline vaults, multi-factor approvals (multi-signature transactions), tamper-proof hardware, and geographically distributed backups.
- Compliance & Trust: Meets KYC/AML and licensing requirements, ensuring institutions operate within global standards.
- Institutional Confidence: Provides enterprise-grade controls, reassuring investors, boards, and regulators.
- Efficiency: Streamlines operations with APIs, automation, and reporting, reducing manual back-office work.
- Growth: Bridges crypto with traditional finance, enabling safe adoption at scale.
Security
Attackers target keys, change recipient addresses, or exploit approvals. Enterprise custody reduces these risks with segregated environments, multi‑party approvals, tamper‑evident hardware, transaction policy engines, and geographic redundancy.
Compliance
Rules have sharpened. In the EU, MiCA applies in two phases. Stablecoin provisions apply from 30 June 2024. Broader rules for crypto‑asset service providers apply from 30 December 2024. In the U.S., new accounting rules require many entities to carry qualifying crypto assets at fair value with changes in net income starting fiscal years that begin after 15 December 2024. New York’s regulator emphasizes segregation of customer assets and clear disclosures for sub‑custody. Across jurisdictions, the Travel Rule now applies to crypto transfers, with EU guidelines effective December 2024 and FATF urging stronger enforcement.
Operational resilience
EU DORA applies from 17 January 2025 and raises the bar for ICT risk management, incident reporting, and third‑party oversight for financial entities and their critical ICT providers. If you serve EU firms, your custody operations must align.
Expert view
FASB: “measure certain crypto assets at fair value, with changes in fair value recorded in net income.”
FATF: “less than one third have issued findings or directives” on Travel Rule enforcement, highlighting the need for stronger controls.
Types of Custody
Custody models you can run
1) Self‑custody with vendor support
You keep key‑control and run the system within your perimeter. Use cases: banks, market infrastructure, large fintech. You gain autonomy and reduce counterparty risk. You also accept responsibility for governance, controls, and audits.
For businesses that prefer direct control, Scalable provides turnkey key management tools and expert guidance. You retain full ownership of your cryptographic keys while leveraging our secure hardware and software frameworks. Our team assists with setup, backup strategies, and policy recommendations - ensuring you avoid the single-point-failure risks of unmanaged key storage. This approach suits organizations with internal technical capability that want autonomy without taking on excessive security or compliance burdens alone.
2) Qualified third‑party custody
A regulated custodian safekeeps assets, while you integrate by API and policy. Use cases: funds, brokers, corporate treasury. You benefit from the custodian’s licensing, controls, and insurance. You trade off some control and custom policy design.
In this model, Scalable Solutions sets you up through a partnership network of the custodians acting as a reliable technological provider through. Partner-custodian holds and protects your digital assets in industry-leading, fully reserved vaults. You benefit from our proven security infrastructure, regulatory compliance, and professional liability coverage without necessity to hold a custodian license yourself.
Outsourcing custody to Scalable’s partner ecosystem eliminates the need to build or maintain in-house key management, allowing your business remain with monitoring performance and adhere to oversight best practices.
3) Collaborative custody
You co‑manage key shares with a technology partner or custodian. Transactions require a threshold of approvals across parties. This reduces counterparty risk while keeping operational control and rapid recovery.
Scalable co-manages key shares alongside your team using a multi-signature framework. Your business holds the majority of key approval power, while Scalable safeguards the remaining key shares. This arrangement balances operational control with third-party oversight and insurance, reducing counterparty risk without sacrificing self-custody benefits. It is ideal for enterprises requiring both high security and active involvement in transaction approvals.
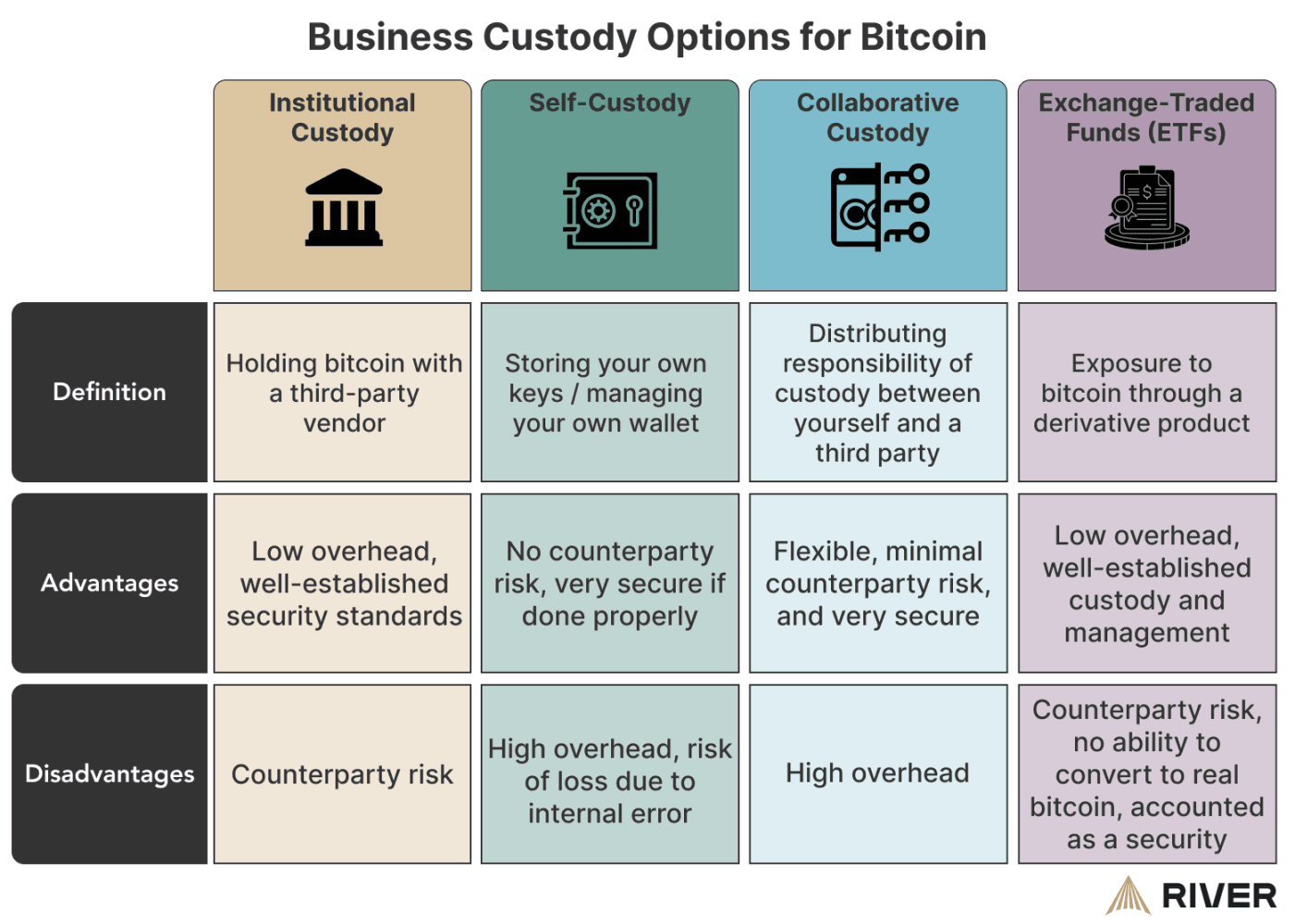
Source: https://river.com/learn/how-should-a-business-store-bitcoin/
Deployment options
Option A: Hosted service in a dedicated environment
Faster to launch. Vendor manages infrastructure and security baselines. Your team manages policies and approvals.
Option B: Dedicated VPC in your cloud
You host the stack in an isolated VPC. Strong for compliance alignment and integration with your SIEM, KMS, and IAM.
Option C: On‑prem
Highest control, longest lead time. For entities with strict data residency or air‑gapped vaults.
Security architecture that stands up to audits
Key management and cryptography
- MPC and threshold signatures to split trust across devices, teams, and sites. Modern schemes such as FROST formalize two‑round threshold signing and support high throughput.
- HSMs validated to FIPS 140‑3 or 140‑2 for hardware key protection and secure entropy. FIPS 140‑3 defines “four increasing, qualitative levels of security,” which auditors recognize.
- Crypto agility and PQC readiness. Maintain inventories of cryptography, plan migration, and test NIST‑standardized PQC algorithms in non‑production today.
Policy engine and approvals
- Per‑asset, per‑desk, per‑jurisdiction policies
- Multi‑level approvals with quorum rules and device attestations
- Velocity, destination allowlists, geofencing, and time locks
- Automated screening with KYT and Travel Rule data exchange
Environment and monitoring
- Segregated networks and bastion access
- Immutable logs to your SIEM
- Continuous monitoring for anomaly detection and sanction risks
Business continuity
- Site‑level redundancy with independent quorum paths
- Key‑share backup with tamper‑evident media and test restores
- Crisis runbooks covering loss of quorum, vendor outage, or key compromise
How modern custody actually works
- Initiation A user or system submits a withdrawal, transfer, or settlement instruction through API or console.
- Screening The platform checks KYT flags, Travel Rule data, destination allowlists, and rate limits.
- Policy evaluation The policy engine maps the request to an approval path and collects independent approver attestations.
- Threshold signing MPC or HSMs generate a signature only after policy checks pass. No single device can sign alone.
- Broadcast and reconcile The transaction broadcasts on chain. Reconciliation, accounting, and risk reports update in near real time.
- Audit trail Every step produces immutable logs for SOC 2 and ISO 27001 evidence.
Compliance map for 2025–2026
- MiCA. Stablecoin rules in force since 30 June 2024. CASP rules apply from 30 December 2024. Validate licensing and whitepaper duties, custody controls, and capital where relevant.
- FASB ASU 2023‑08. Fair value measurement and disclosures for qualifying crypto assets. Effective for fiscal years beginning after 15 December 2024. Align finance, risk, and product teams now.
- NYDFS Custody Guidance. Segregation, limited purpose possession, sub‑custody approvals, and disclosures. If you operate under BitLicense or as a limited purpose trust, align your controls.
- Travel Rule. EU guidelines effective 30 December 2024. Implement interoperable data exchange and exception handling across VASPs.
- DORA. Applies from 17 January 2025. Map ICT risks, test incident response, and manage third‑party risk for custody stacks.
Practical enterprise use cases
- Hold reserves, run payments, and sweep idle balances into tokenized T‑Bills with policy governance and real‑time reporting. RWA data shows this market now operates at multi‑billion scale, which improves liquidity and counterparty choice.
- Isolate client funds, automate hot‑to‑cold flows, and enforce withdrawal policies with KYT and Travel Rule data exchange.
- Support fund accounting, NAV, and trade settlement with SOC 2 evidence, FASB fair value disclosures, and controlled access.
- Protect reserves and program wallets, enforce issuer policies, and meet MiCA and Travel Rule obligations for flows and attestations.
- Manage issuer keys, transfer restrictions, and recovery processes for compliant secondary transfers.
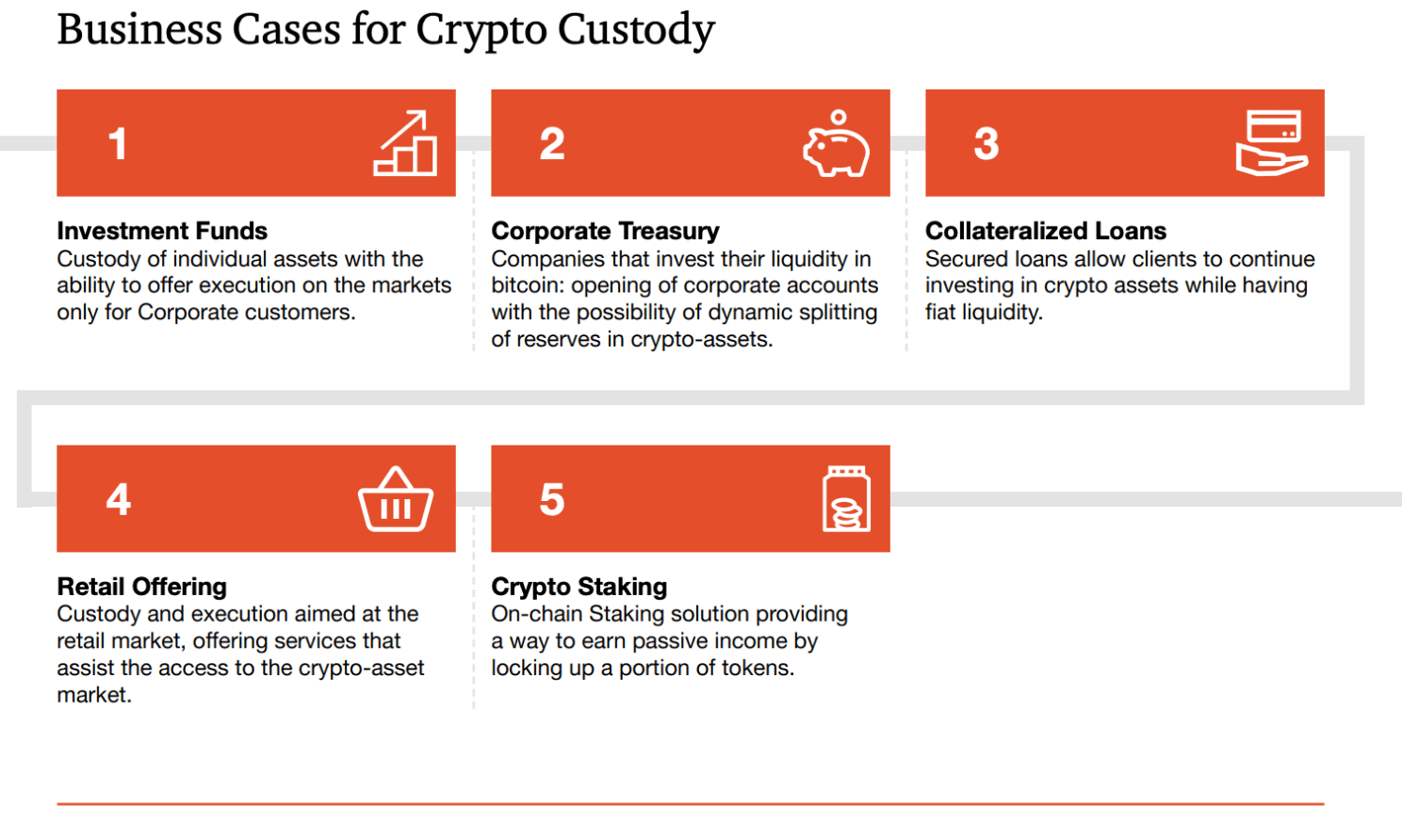
How to choose the right solution
Decision matrix
Regulatory posture. Do you need a qualified custodian or can you self‑custody with controls and audits
Operating model. Do you prefer hosted service, dedicated VPC, or on‑prem
Risk tolerance. What loss scenarios are acceptable. What quorum model limits that risk
Performance. What are your peak TPS, approval latency targets, and SLA needs
Integration. How will it connect to core banking, ERP, markets, and analytics
FAQ
What is the difference between MPC and multisig
Multisig is enforced at the blockchain layer and depends on chain support. MPC creates one signature from multiple fragments and works across more chains. MPC improves key recovery and rotation.
Do I need a qualified custodian
If your regulator or mandate requires it, yes. Otherwise, many institutions operate compliant self‑custody with SOC 2 evidence and strong policy. Check MiCA and local rules.
How does the Travel Rule affect withdrawals
You must exchange originator and beneficiary information with counterparties and handle exceptions when data is missing or counterparties are non‑compliant. Build workflows to block, hold, or remediate.
What accounting treatment applies under U.S. GAAP
For qualifying assets, measure at fair value with changes in net income for fiscal years beginning after 15 December 2024. Disclose holdings and changes.
How should we plan for post‑quantum
Inventory crypto, prioritize systems by exposure, and test NIST PQC algorithms in non‑prod. Maintain agility to rotate algorithms.
What operational standards should we ask vendors to meet
SOC 2 Type II, ISO 27001, and evidence of DORA‑aligned resilience for EU‑facing services.
Glossary
MPC
Multi‑party computation splits key control across devices or teams so no one can sign alone.
Threshold signatures
A signature appears from a threshold of participants. FROST is a modern design.
HSM
Hardware Security Module that protects keys in tamper‑resistant hardware. Often validated under FIPS 140.
Travel Rule
A rule that requires originator and beneficiary information to travel with crypto transfers between service providers.
DORA
EU regulation for digital operational resilience that applies from 17 January 2025.
MiCA
EU framework for crypto assets with stablecoin rules from June 2024 and CASP rules from December 2024.
Conclusion
Treat custody as a control system, not a wallet. Define your risk model, choose the right operating and deployment model, demand audit evidence, and test recovery. If you build with these principles, you protect assets, speed settlement, and stay ready for audits.
If you want to review an architecture or run a pilot, our team will map controls to your risks and regulatory scope, then deliver a deployment plan that you can take to your board and auditors.