Trusted Execution Environments for Digital Asset Protection
%20Site%20(2)-1757620216163.png)
What a TEE actually does
A Trusted Execution Environment is a secure area inside a processor that keeps code and data confidential and intact, even if the host OS is compromised. Or as the Confidential Computing Consortium puts it, “Confidential Computing protects data in use by performing computation in a hardware‑based, attested Trusted Execution Environment.”
“At its simplest, a TEE is a secure area within a processor. It guarantees that the code and data loaded inside it are protected with respect to confidentiality and integrity.” — Confidential Computing Consortium
TEE guarantees you rely on:
Isolation: Sensitive code runs in a hardware‑isolated context.
Attestation: Remote proof that the right code runs on genuine hardware before it receives secrets.
Sealed storage: The enclave binds data to hardware so only authorized code can open it.
Architectures you can deploy today
Intel TDX: Confidential VMs with remote attestation integrated through services like Intel Trust Authority and cloud attestation profiles.
AMD SEV‑SNP: Encrypts and integrity‑protects VM memory to mitigate hypervisor‑level attacks. Mainstream Linux distros and clouds support it.
Arm CCA: Introduces Realms for isolated execution on Armv9 platforms, evolving the TrustZone model.
Cloud TEEs: Managed offerings like AWS Nitro Enclaves bring enclave patterns to EC2 without extra hardware.
Why hardware isolation now
Attackers target key material, trading logic, and control planes. The numbers are clear:
2024: Stolen crypto rose 21% year over year to $2.2B.
Reuters
H1 2025: Stolen funds exceeded all of 2024 mid‑year, driven by record‑setting exchange breaches and state actors.
TEEs reduce the blast radius of supply‑chain compromises, insider abuse, and kernel‑level malware by locking sensitive operations inside attested hardware.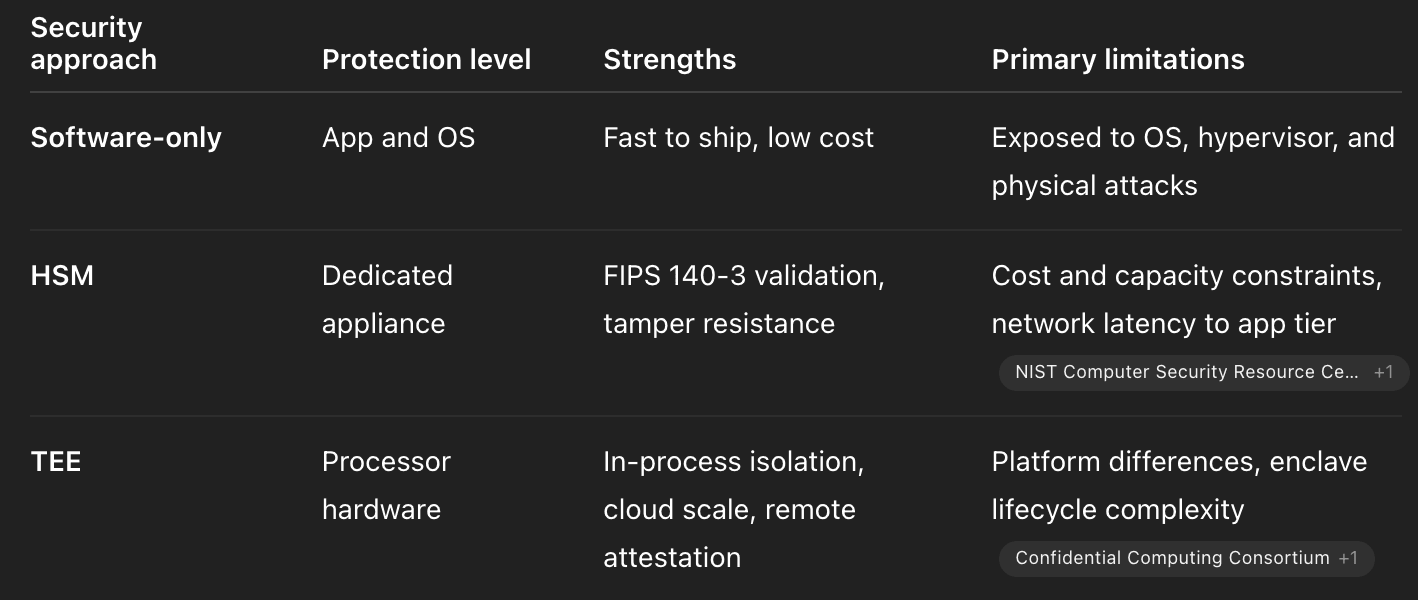
You do not replace HSMs everywhere. You combine them. Use HSMs for root‑of‑trust and compliance boundaries, and run wallet logic, policy engines, and TSS signing flows inside TEEs to minimize exposure and latency.
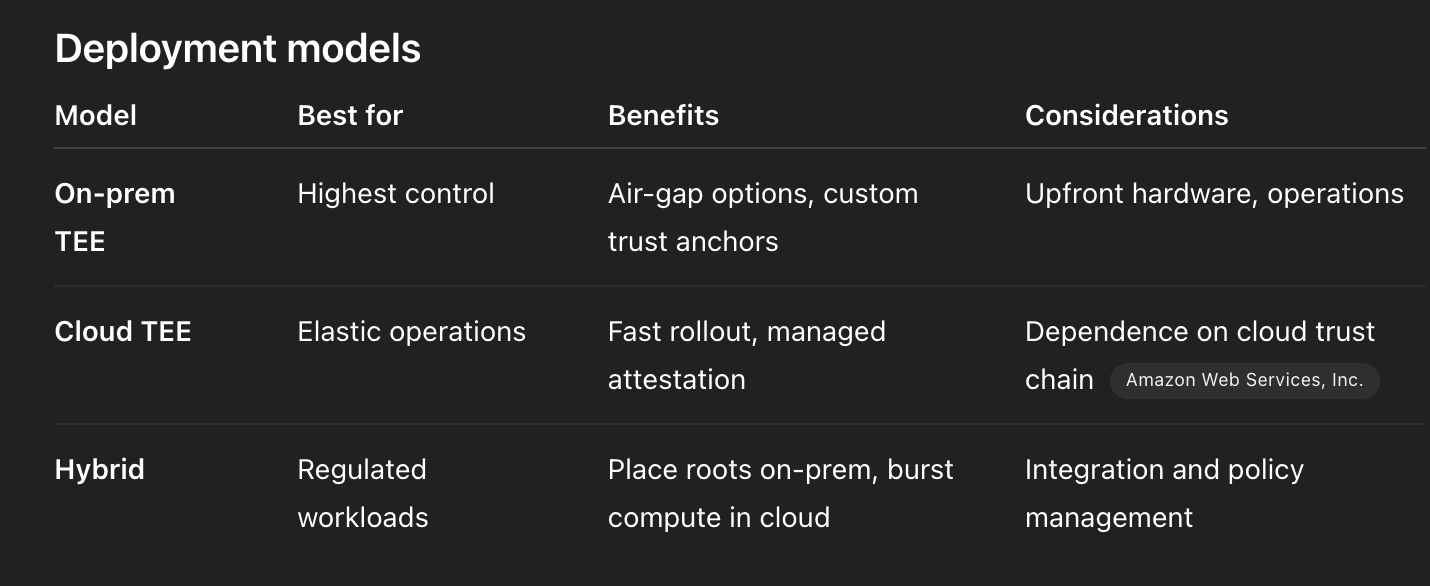
Architecture patterns for digital asset custody
Scope what goes into the enclave
Key material and policy checks: Derivation, wrapping, and policy evaluation stay in the enclave.
Pre‑broadcast controls: Risk, limits, and sanctions checks run before signatures leave the enclave.
Sealed audit: Write tamper‑evident logs from the enclave to append‑only storage.
Attestation and secret release
- Verify measurements on boot and before every sensitive action.
- Release KMS keys or secrets only on valid attestation claims from TDX or SEV‑SNP.
Multiparty and threshold schemes with TEEs
TEE‑backed TSS: Hold key shares across multiple enclaves and clouds to remove single points of compromise.
Separation of duties: Assign operators to independent attestation domains and require thresholds for approvals.
Compliance signals regulators look for
Regulators expect strong internal controls, auditable change, and protection of sensitive data. TEEs help you show:
Integrity of keys and code paths through attestation records.
Cryptographic module assurance when paired with FIPS‑validated components.
Privacy‑preserving processing for AML, KYC, and PII workflows under GDPR and EU MiCA.
Operational resilience aligned with Basel III operational‑risk expectations.
Market signals and adoption
Market estimates vary because vendors define “confidential computing” differently. Treat them as directional:
Grand View Research: $5.46B in 2023, 64.1% CAGR to 2030.
Fortune Business Insights: $24.24B in 2025, $350.04B by 2032, 46.4% CAGR; North America ~50% share in 2024.
On the HSM side, multiple firms project a steady climb to $4–5B by 2032. Expect blended stacks where TEEs front‑end HSM roots.
Implementation checklist
Threat model: Identify what you protect, from which actors, and where compromise is likely.
Pick your TEE(s): Intel TDX, AMD SEV‑SNP, or Arm CCA, aligned to your platform and cloud.
Attestation first: Enforce policy‑gated secret release and workload identity.
Microsoft Learn
Key hierarchy: Keep roots in an HSM, run hot‑path signing and policy in TEEs.
Observability: Capture enclave measurement changes and write sealed audit logs.
Fail‑safe operations: Define break‑glass flows with strict quorum and time‑locks.
Red‑team: Test side‑channels and operator workflows, not just crypto.
Strategic recommendations
Evaluate TEE integration in your custody and trading stack within this quarter. Design for regulatory evidence - store attestation and policy decisions as first‑class artifacts. Train engineering on enclave lifecycle, attestation, and secure build. Adopt a hybrid trust model: HSM roots plus TEE‑based policy and TSS for scale. Abstract attestation and secrets to avoid lock‑in across clouds and CPU vendors.
What’s next
Expect better tooling, broader Arm CCA availability, and deeper cloud integrations. You will still manage platform differences, performance trade‑offs, and specialized debugging, but the security payoff is clear.
FAQ
What’s the difference between a TEE and a confidential VM?
A confidential VM uses CPU extensions like TDX or SEV‑SNP to isolate the entire VM from the hypervisor. A classic TEE often isolates a process or enclave. Both deliver hardware‑enforced isolation with attestation.
Do TEEs replace HSMs for custody?
No. Keep your root keys and compliance boundaries in FIPS‑validated modules. Use TEEs to run policy, risk checks, and hot‑path signing with lower latency and better scale.
Which clouds support TEEs?
Major clouds provide options like AWS Nitro Enclaves and confidential VM types backed by Intel TDX or AMD SEV‑SNP, plus native attestation services. Check your region and instance families.
How do I prove to auditors that a TEE is working?
Collect attestation evidence for every deployment and action, store it immutably, and map those records to your control objectives. Pair with CMVP or Common Criteria validations where applicable.
Are TEEs vulnerable to side‑channel attacks?
Vendors continuously harden against side channels, but you should still minimize enclave TCB, review code paths, and red‑team with realistic traces. Use current microcode and cloud guidance.
Is Arm TrustZone the same as Arm CCA Realms?
No. TrustZone splits secure and non‑secure worlds. Arm CCA introduces Realms for confidential VMs that are opaque to the OS and hypervisor.


